
Yesterday I attended a fascinating talk in London that was organised by the Institute for Democracy and Conflict Resolution, a part of the University of Essex. I have been on the look out for free lectures to attend and “New Technology and Human Rights” leapt out at me so I signed up straight away. I anticipated a discussion mostly about Twitter and Facebook, but it really went much deeper than that. Overall an excellent seminar.
The talk was chaired by its director, Prof. Todd Landman, and featured representatives from Frontline SMS, Cyberalpha, Maplecroft and the German Development Institute. Each of the speakers explained how their research and services are being used in the fight against human rights abuses.
The key to the discussion was the use of new technology and how it can both empower and educate. Buzz words for the day were crowd sourcing, filtering of information, geotagging, corporate responsibility, self-disclosure, media richness, online censorship.
Some interesting questions were raised in the Q&A session, such as “why is human rights information so bad?” and “how to get a message to become viral?”. This was a very interesting point as it is something that both commercial enterprises and social, political and human rights groups also need to understand – to spread a message far and wide it needs to be “viral” in this modern era. That means it needs to be shared across a wide range of media by a diverse group of people. A lot of what is termed “viral” on the Internet is really not viral at all, as it is only shared enthusiastically by a single niche in the community. More on that later, here are my notes from the seminar.
Ken Banks – FrontlineSMS
Ken Banks is the founder of FrontlineSMS, an innovate tool that allows people to use a mobile phone SMS to quickly communicate messages to many people. Ken is read Social Anthropology with Development Studies at Sussex University and believes that understanding people is the real key to understanding the new social age of technology.
Ken has lived in Africa for many years and while there he decided that the Internet was not an ideal solution for communication as there are so many black spots. However, almost everywhere you go you can pick up a mobile signal. This service requires a mobile phone and a basic laptop to run.
“If you can build stuff that doesn’t require the Internet you can use it anywhere” ~ Ken Banks
The slogan on the FrontlineSMS website is “using mobile technology to promote positive social change“. Ken explained how FrontlineSMS started out as a way for villagers in to send warnings to each other of simple local issues such as elephant stampedes (which are still a serious problem in some parts of Africa). Today it is used in human rights, disaster relief, election monitoring, health and many other areas. In 2007 it was used to monitor the Nigerian elections (read about it on the BBC News: Texts monitor Nigerian elections.
Ken always focussed on making FrontlineSMS a tool that anyone can use. This means that it is simple and intuitive to use, and Open Source (free to download and use). He never actually planned it to be used the way it is, but if supporting its use in all areas. His approach to social technology is “letting users get on with it and not interfering“. He builds the platform and then waits to see what people do with it, and then supports that use. An important lesson here for industry!
One of the key features of FrontlineSMS is in geomapping. As people send messages this creates an alert on a map, providing a geographical reference. In terms of human rights, this can quickly alert people to the whereabouts of new human rights abuses as people report beatings, executions, rapes and other human rights violations.
FrontlineSMS does still have some obstacles. It does not support all languages (it started out as just English) so now any literate person with access to a mobile and laptop can use it. However, illiterate people are still unable to use it effectively. They are hoping to utilise voice-to-text technology in the future. With a full Internet service visual icons can be used (Jonathan Crook’s Cyberalpha system uses icons), however, with text only this is not possible.
HarassMap.org – a FrontlineSMS Success
HarassMap uses FrontlineSMS and Ushahidi to monitor and map harassment in Egypt. HarassMap was founded by Rebecca Chiao who has lived in Egypt for 7 years and works in the field of gender discrimination. For Rebecca the main purpose of HarrassMap is to change attitudes of harassment in Egypt. She explains in an interview with Ken:
“There is a social acceptability surrounding harassment on the streets; people will often stand by and let it happen” ~ Rebecca Chiao, HarrassMap.org.
You can learn more about this product on the FrontlineSMS blog post: Mobile phones give harassment victims a voice in Egypt.
Jonathan Crook – Cyberalpha
Cyberalpha provides technology solutions for information management, analysis and visualization. It was developed by Jonanthan Crook who spent 20 years in the British military, working in a variety of conflict zones including Iraq and Afghanistan. In conflict zones the rapid flow of information is vital for survival. Cyberalpha is based at the University of Essex. It was founded in 2010 and in June 2011 it won a UK Government innovation competition.
Jonathan explained how military learning is being used in the development of tools to increase human rights awareness.
OODA: Observe, Orientate, Decide, Action
OODA is an acronym for Observe, Orientate, Decide, Action. It is a feedback loop that people instinctively use in all situations. Any failing in a part of the loop slows down decision-making. In social media and technology information overload is one of the biggest problems, so analysis and filtering of information required to provide useful data on which to act.
Cyberapha use a range of technologies such as Twitter monitoring, geotagging and semantic text analysis to gather information on what is really happening on the ground. Ontology is a key aspect of the programming behind Cyberapla.
Jonathan Crook explained that a philosophy of Cyberalpha is to “let people self determine“.
One feature of the Cyberapha system is that people can alert the network to human rights abuses by using icons rather than words. These can quickly build up a picture of events as they happen which is then reported back to the central computers. For examples, people in Mexico have used the system to report kidnappings, executions, crowd control and torture.
Mapping and spatial visualization is vital in understanding and acting on information concerning human rights abuses.
Mandy Kirby – Maplecroft
Maplecroft create an annual Human Rights Risk Atlas, along with several other risk atlases including risks in the legal and regulatory field, natural hazards, climate change, deforestation he the industrial sector. The objective of Maplecroft is to index, analyse and map risk. Maple croft started as a project at the Warwick Business School and still use a team of developers and designers to manage the entire project in-house. They have their own GIS, software and design teams to process the data and produce the maps.
Maplecroft monitor around 500 individual risks globally, of which 31 are human rights indicators. 6 months of data gathering is used in each Atlas.
Maplecroft have found that Human Rights issues have been worsening in 2011. Areas of increased abuse are in land rights, women and girl rights. Many of the abuses are thought to be stemming from mass movements of populations and military actions resulting from the Arab Spring.
Human trafficking is also monitored and mapped. This information is used by commercial enterprises to better understand the environments in which they already operate and those in which they are considering entering. Currently India experiences the most cases of human trafficking and enforced labour in the world. Mandy Kirby showed how risk maps can be overlaid with geological maps, which is something I found fascinating, as I am a Geographer (got a two-one) at heart.
Maplecroft are not building real-time alerts like Cyberalpha and FrontlineSMS, but they are still utilizing social media and new technology to gather data from a wide range of sources, scrub that data (sanitize, filter etc.) and publish in a format that can be used to make decisions on the ground.
Anita Breuer – D.I.E. (German Development Institute)
Dr. Anita Breuer works in the Department of Governance, Statehood, Security at Deutsches Institut für Entwicklungspolitik (DIE) in Bonn, Germany. Her most recent research is on the impact of social media on political participation, The key elements in her findings concern Self Disclosure and Media Richness.
Anita Breuer’s spoke largely about Social Media and Protest Mobilization in Tunisia and how social media was being utilized long before the Arab Spring to allow people in Tunisia to communicate with each other. During the late 1990’s the Tunisia government started censoring the Internet, however this gave rise to many social blogs and websites that were set up to bypass this.
One was Takriz.com, which is hosted outside of Tunisia (hosted by Godaddy) and managed by ex-pats who are relatively immune to any repercussions (I say relatively, as Jonathan Crook warned in the final discussions that “regimes have long tentacles“). Takriz is a “free citizen movement Tunisian government censored criticism of Internet censorship in Tunisia dictatorship to freedom of expression and press” – a Google translation.
They also have a Facebook page, www.facebook.com/takrizo, where they describe themselves as “Tunisian cyber think tank & street resistance network since 1998. Free, True & Anonymous – Takrizo Ergo Sum – We make revolutions!“. It currently as 86,984 users and over 2000 people are talking about it on Facebook at the moment (16/12/11).
Nawaat – the Power of Collective Blogging
Anita talked about how Collective Blogs are playing a more important role in spreading information, news and helping people to network. Collective blogs, which are blogs much like WordPress powered ones, where there is a small team of administrators and editors who control the content, then many authors and contributors who update the blog.
The main collective blog that the people of Tunisia have turned to is Nawaat.org. “Nawaat.org is an independent group blog run by Tunisians. It gives voice to all those who, through their civic involvement, take it, wear it and broadcast. Our editorial decisions are guided by among other concerns that affect the daily lives of our countrymen and our fellow men.” (from the Google translation of their homepage).
Nawaat was set up in 2004 and has a team of around 5 admins (who all live outside of Tunisia) and 500 contributes. Comments are open, so anyone with access to Nawaat.org can participate in a discussion – just like you see here on Webologist.co.uk.
The advantage of collective blogging is that there is far more trust in what is said. Many people are wary of what they read on Facebook Twitter. Is is a fact that governments and other organisations manipulate conversations online. A great example given by in the Q&A session afterwards was that the Putin’s PR team have allegedly set up many fake Twitter profiles to drown out the pages of protesters by auto-Tweeting pro-Putin messages. This is a simple form of reputation / brand management – shout louder than your critics and people will hear you. In a collective blog, all posts have to be approved by the core team of editors before they are published, so external manipulation is not possible. Tunisia has blocked access to these blogs but some readers know how to get around that using proxy servers.
Many of the contributors to Nawaat also have their own blogs making it a very well-connected network. Apparently all blogs are blocked inside Tunisia. Facebook remains one of the few open channels to people inside Tunisia without knowledge / access to proxy servers. Although many people are understandable reluctant to participate on that channel. However, many people do upload mobile phone photos direct to Facebook. I think that there may be an open email address to use, so uploads are effectively anonymous and cannot be traced back to individuals, so long as Facebook does not decide to cooperate with requests from government – this needs to be clarified, but the sites are all in French and I cannot understand them!
Breaking the National Media Blackout
The complex network of social media channels, with many out of the control of the Tunisia government, means that people are able to bypass the media blackout. One example given was that people in the UK and other European countries could update Facebook with events as described to them over secure channels (see Mumble below) and then these would be picked up by news organisations such as Aljazeera and then broadcast to the people of Tunisia.
Facebook also became a focal to find like-minded people opposing the regime.
Cost-Benefit Analysis of Participation in Revolution
This sounds complex, but in reality it is a simple process that mostly works on gut reaction. The idea is that an individual will never participate in a protest if they feel that the personal risk to them is greater than the collective benefit of that protest, i.e. democracy. Or, most people are survivors not martyrs!
Social media played a vital part in encouraging more people to take to the streets, as once the initial images were shared showing thousands of people protesting, other people felt that it was relatively safe to join the protests. A few hundred people can be kettled and arrested (or beaten, shot etc) but tens of thousands is another matter altogether – safety in numbers has been a key part of human survival and evolution.
Images on Facebook could show cases where “free riding” was possible. Free riding sounds a little negative, but it refers to the point in a protest where it is deemed safe for an individual to join in without fear of harm coming to them from the authorities that they are protesting against. It is thought that when photos were first posted to Facebook of the revolutions in Tunisia this formed a turning point as suddenly everyone who was against the regime felt confident to stand up be counted.
Mumble – Encrypted Communication
One tool that Anita mentioned is Mumble. Mumble offers voice communication with a difference – it is encrypted to improve the privacy of those speaking. All communication with Mumble is completely encrypted (s2c). The control channel is encrypted with TLSv1 AES256-SHA while the voice channel is encrypted with OCB-AES128 (source: Mumble/Murmur over SSH on Sourceforge.net).
They offer the service through their website, Mumble.com, and they also allow you to download the software and install it on your own servers (it runs on Windows, Mac OS X and Linux). Mumble was developed by the gaming community to allow people to coordinated themselves, but like Ken Banks’ FrontlineSMS, people soon found alternative uses for it, possibly including organizing protests.
Self Disclosure and Media Richness
Dr. Anita Breur explained how the relationship of self disclosure and media richness determines when action is taken. Here is a diagram to help explain:
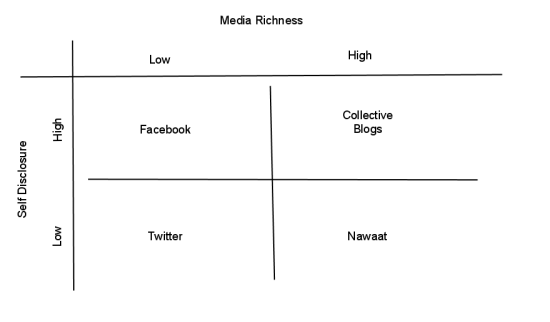
This helps to show why sites such as Nawaat are so useful. They provide a media richness, which is partly defined by quality of information and trust, and limited self disclosure. Collective blogs are generally a little riskier.
Facebook is not only risky but is consider lower quality in terms of media richness (it can be manipulated and closed down). There are too many unqualified people giving their opinion on Facebook, and verification of facts is next to impossible at times.
Twitter is relatively safe to use (especially if you set up a webmail address solely for your social media activities – something that everyone should consider really, not just activists and protesters).
The Q and A Session
The question and answer session at the end raised many more interesting topics. If I had time I would insert where relevant in the posts above, but it is easier, and possibly fairer on the speaks, to keep it separate.
The Problem of Illiteracy
The first question was on the problem of illiteracy. Many of the most vulnerable people are simply not able to participate in social media at the moment. There are movements into providing more Voice to Tweet services. In fact, Google have very recently launched a service that allows people to create Twitter messages from voice. The purpose was to increase safety in Tweeting.
“anyone can tweet by simply leaving a voicemail on one of these international phone numbers (+16504194196 or +390662207294 or +97316199855) and the service will instantly tweet the message using the hashtag #egypt. No Internet connection is required. People can listen to the messages by dialing the same phone numbers or going to twitter.com/speak2tweet.” Google Official Blog.
What is great is that this is a collaboration between Google, Twitter and SayNow (which is now a part of Google) specifically to help people in Egypt. The same system could be rolled out to aid many other people suffering human rights abuses, or in fact, anything else.
How can technology provide objectivity?
This was actually asked by Jonathan Crook and is a vital part of using technology to monitor, analyse and respond to human rights issues. For every message across social media there is a person, but to act you need to be sure that the facts are correct and not being misrepresented, exaggerated or simply abused to get a response.
We are drowning in data!
Ken Banks said that we are drowning in data. The biggest challenge is not so much in encouraging the use of social media (although there are still many people without access) but in understanding how to turn a sea of noise into a usable message. Ken mentioned the Data Without Borders group who take in vast amounts of data and then visualize it for human consumption (I think that they are http://datawithoutborders.cc/ but I am not sure if that is the right domain!).
How do we reduce barriers of fear?
A representative from Freedom from Torture asked the panel for ideas on how we can reduce the barrier of fear to encourage more people to share their stories and experiences.
It was then that Jonathan Crook reminded us that “regimes have long tentacles”. There are many problems with the current systems as so much information can be traced. IP addresses, Facebook profiles, mobile phone numbers etc. they can all be traced back to people.
Todd also asked “The silent people – what to do?”. So many people are without a voice and one criticism of these maps that are generated from social media is that all we really learn is where the mobile phone are!
The Danger of Social Media
“The biggest danger is that people do no know what danger they are putting themselves in” ~ Ken Banks.
“It is important to train people in the safe use of these tools, social media is a double-edged sword” ~ Dr. Anita Breuer
Why is information on Human Rights so Bad?
One member of the audience asked this question. Even in this day of mass social media, many people are still so ill-informed on what is really happening in the world. Human Rights is a huge area of discussion. Violations take place constantly in every country in the world, there are no places devoid of human rights violations. And yet, so little is reported.
It was discussed how the mainstream media tend to focus on the big numbers and ignore the stories that they feel will have a smaller impact. These leaves huge areas of data / information missing from the public eye.
Technology and the Economic Downturn
The role of social media and the failing economy was touched upon. This is the first economic crisis where people have had such a loud voice. Protests have always followed economic problems, but in the past protesters would be removed and ignored. Classic examples are the protesters of Occupy Wall Street and the St. Paul’s protesters. We are seeing images, both photos and videos, almost daily of abuses inflicted by the police in America, on American citizens that are peacefully protesting.
Who is a Reliable Source of Truth?
Caroline Ford from the BBC World Service Trust (one of the only full names I managed to note down) asked about how trustworthy any information is and how to know when, or if, information has been manipulated. There seems to be a lack of attention to how technology is being abused by people wanting to disrupt the actions of others. Crowd Sourcing is a fantastic way to gather information, but it is open to abuse.
This lead to the discussion of how people do not really reach in social media. Anita Breur explained that it is a misconception that social media builds links. In reality, people befriend those that are most similar. Like minded people stick together and develop cliques – social media helps close-minded people find other close-minded people!
Ken Banks explains that the misuse of information is really a “judgement call”. His platform gets used to break the law, but it is his belief that developers should remain impartial. It was very difficult to control once a tool is out there.
Prof. Todd Landman described “truth” as being “estimation and a margin of error“. We approximate the truth.
Social Media Must Lead to Action
As a final note, an amusing comment was made by either Jonathan Crook or Ken Banks (I wish I could remember which!) at the end of the question session. It went something like this:
Social media is only useful if it leads to action. Revolution only works when people take to the streets and protest en masse. If 100,000 people “Liked” a Facebook page called “We hate Mubarak” nothing would have changed.
It was the only comment of the day to get any laughs. Human Rights is not a subject you can easily make fun of!
The best business insight really came from Ken Banks;
“Make it for the lowest common user and the rest will work itself out.“
In the world of web development and marketing many people use the acronym KISS (Keep It Simple, Stupid! or maybe Keep It Short and Simple) to remind themselves and others of this concept.
Final Remarks
This was the first seminar of this nature I have ever attended and glad to report that it was a fantastic experience. I only discovered it while researching for interesting events to report on for my EssexPortal.co.uk website!
Of all the discussions the thing that really impressed me the most was Ken Banks’ Frontline SMS. This is a service that allows people to communicate as effectively as Twitter but without an Internet connection. While Google talk about distribution Chrome OS laptops to people all over the world, to get the world connected, they seem to be missing a vital point – many, many people do not have Internet access. However, you can pick up a mobile signal is some of the most remote places.
Maybe one day the Internet will be as available as mobile. Maybe one day there will be only one service and mobile networks and Internet networks will merge and become as one. This really would give everyone access to social media and the opportunity to report what is happening and decide how to respond to changing events, or as Jonathan Crook would put it, Observe, Orientate, Decide, take Action.
Many thanks to the University of Essex for organising this event. Here are some useful links:
- http://www.essex.ac.uk/ – Essex Uni main site!
- http://www.idcr.org.uk/ – Institute for Democracy and Conflict Resolution (IDCR)
- http://www.frontlinesms.com/ – Frontline SMS
- http://www.cyberalpha.co.uk/ – Cyberalpha
- http://maplecroft.com/ – Maplecroft
- http://www.die-gdi.de – Deutsches Institut für Entwicklungspolitik
btw that diagram was a quick mashup on Google Docs using Drawing, which may explain why it is a bit wobbly.
Great write-up on a great event.
One minor correction from my Q&A comment. I didn’t say that developers of tools weren’t accountable, but that it was very difficult to control once a tool is out there. A guide helping activists circumvent authoritarian regimes is equally as useful to a gang of arms traders. We need to be aware of these problems and wherever possible limit any negative impacts.
Ken
Cheers Ken, I have edited that line.
One thing that stuck in my mind was the image of a laptop with a mobile connected. With improvements in mobile phones, and open source platforms like WebOS as well as Android, could FrontlineSMS soon work without the need of a laptop at all? And it the laptop only needed to manage the messages? I assume individuals with phones just send a text to a central area? It was only after the event that I started to wonder how it all actually works.
This is a wonderful and comprehensive review Jon. Many thanks for coming to the event and making it a success. I have added this URL to our news blog on the IDCR website at http://www.idcr.org.uk
Again many thanks for coming. Keep an eye on our wesbite for more developments!
Best wishes
Todd
Professor Todd Landman
Director
Institute for Democracy and Conflict Resolution
University of Essex
http://www.idcr.org.uk
I will certainly keep an eye out. I passed this on to a friend in America, and he was surprised to learn that you work for Essex. He is distributing it around to his students as we speak.
If all seminars are as good as this one was I will definitely be keeping a beady eye out. Hmmm, that gives me an idea.
Very sorry for not being able to attend this event in person. Really wanted to find out how we could make our new crowd-sourced initiative (called Bijoya)to report incidents against women in Bangladesh more effective.
That looks like a great project Shehzaad. I have made a screenshot to entice readers to take a look:
bijoya.crowdmap.com/main:

Many thanks for doing this Jon, much appreciated.
Dear Shezaad: you can use our icons to add differentiaton to your maps. Please see:
http://www.idcr.org.uk/resources-links/human-rights-icons
The categories of abuse map nicely onto the categories in our collection. Please email me todd@essex.ac.uk
should you have any questions.
Cheers
Todd